Mac.BackDoor.iWorm used Minecraft server subreddit for command and control.
The Dr. Web report doesn’t say how Mac.BackDoor.iWorm is being distributed to victims of the malware. But its “dropper” program installs the malware into the Library directory within the affected user’s account home folder, disguised as an Application Support directory for “JavaW." The dropper then generates an OS X .plist file to automatically launch the bot whenever the system is started.
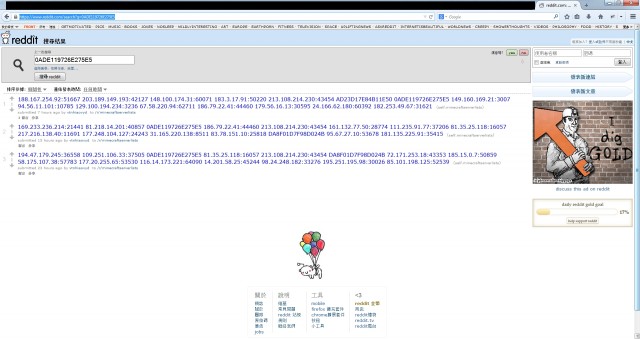
The bot malware itself looks for somewhere in the user’s Library folder to store a configuration file, then connects to Reddit’s search page. It uses an MD5 hash algorithm to encode the current date, and uses the first 8 bytes of that value to search Reddit’s “minecraftserverlist” subreddit’—where most of the legitimate posts are over a year old.
The CnC posts appear to now have been expunged from Reddit, and a survey of the most recent servers identified in the subreddit by Ars found that most of their IP addresses, scattered around the world on systems that were apparently compromised—including computers in Slovakia and at Marist College in Poughkeepsie, New York—are now unreachable. The Marist College node, based on its IP address, was a virtual machine running in the college’s private cloud.
However, it’s unlikely that the botnet has been completely shut down. The malware has the capability of downloading additional files and executing commands on the infected systems, so a new version of the botnet may have already been distributed—along with other malware spread through it.
Security journalist Graham Cluley reports that Dr. Web and Bitdefender both detect variants of the botnet, (which Bitdefender refers to as Mac.OSX.iWorm). There are also ways for Mac owners to defend themselves against the malware. Developer Jacob Salmela has posted instructions on how to create a set of OS X folder actions that will alert a user if their system becomes infected.
No comments:
Post a Comment